As businesses shift to sophisticated cybersecurity models, Secure Access Service Edge (SASE) has emerged as a popular cloud-based solution. SASE combines advanced networking and proactive security features to protect expanding perimeters, including remote and mobile workforces. Fortinet’s solutions for Chinese enterprises showcase the strategic implementation of SASE to ensure secure and seamless connectivity across vast and complex enterprise environments.
SASE merges security and network functionality, enforcing consistent policies and protection, irrespective of user location. It is an essential upgrade for organizations that value performance and security. SASE offers a glimpse into the future of network security, which is flexible, scalable, and inherently secure.
Key Takeaways
- Secure Access Service Edge (SASE) integrates advanced networking and security features to safeguard the modern mobile workforce.
- SASE offers a streamlined approach to cybersecurity that aligns with cloud-centric business models and the ubiquitous nature of internet access.
- Adopting SASE supports business agility and mitigates the complexity commonly associated with traditional security measures.
- Understanding SASE’s current landscape and anticipated evolution can equip organizations to address cybersecurity challenges better.
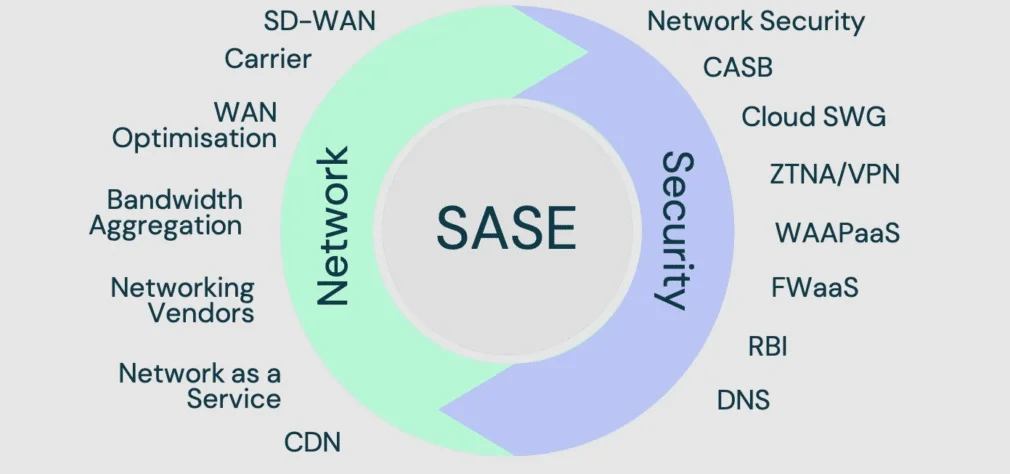
The Components of SASE Architecture
Fortinet’s solutions for Chinese enterprises are based on the Secure Access Service Edge (SASE) security framework. This framework aims to provide comprehensive security through various innovative mechanisms. At the heart of SASE are cutting-edge security components like cloud-access security brokers (CASBs), which act as guardians to ensure safe cloud application use. Additionally, secure web gateways (SWGs) ensure secure internet navigation while firewalls-as-a-service (FWaaS) monitor and control network traffic. Zero-trust network access (ZTNA) is crucial in enforcing a “never trust, always verify” methodology. This is particularly important in a security landscape where threats can emerge from within and beyond traditional network boundaries.
These components are complemented by advanced threat prevention mechanisms and global private backbone networks, resulting in a holistic, unified platform designed to protect against the most advanced threats in our digital-first world.
Furthermore, it is essential to note that SASE’s software-defined architecture relies on something other than hardware as much as previous security frameworks. This feature allows for greater adaptability and responsiveness. It also supports cloud services’ elasticity, allowing enterprises to scale up or down on demand, freeing them from traditional network design constraints.
Implications of SASE on Business Operations
The advent of SASE holds profound implications for business operations worldwide. SASE enables businesses to navigate the modern landscape confidently by unifying network connectivity and cybersecurity services. This consolidation simplifies the cybersecurity environment and makes operations smoother.
It ensures policies are enforced uniformly across all users and locations, enhancing an organization’s security posture and streamlining administrative workflows. SASE eliminates the need for overlapping security services, which brings financial and strategic advantages to organizations. They can enjoy reduced overheads, simplified vendor management, and a holistic view of their security operation.
Additionally, SASE is intimately tied to data protection and compliance adherence. Its architecture enables granular control over data flows, ensuring sensitive information is tightly secured and governance regulations meticulously upheld.
A growing concern among businesses today is their ability to protect their assets in a world rife with sophisticated cyber-attacks. SASE’s unified approach provides the peace of mind that businesses need, ensuring that their data is protected consistently regardless of where it resides or is accessed.
Advantages of SASE for Remote and Mobile Workforces
The shift towards remote and mobile workforce models has been one of the most striking business transformations. SASE emerges as a pivotal technology in this context, providing a secure rudder steering the burgeoning mobile workforce towards safe harbors.
By establishing a zero-trust security model, SASE ensures rigorous authentication and authorization processes for every access attempt, minimizing the chances of unauthorized entry. Consequently, businesses can confidently extend their reach to remote workers without compromising the sanctity of their internal networks.
Implementing SASE simplifies IT management by consolidating multiple security functions into a single cloud-native platform. This centralization enhances the security landscape and elevates the end-user experience.
Employees are empowered with frictionless access to their needed resources, vastly improving productivity and satisfaction. The agility and user-centricity that SASE brings make it an invaluable asset in the quest for a balanced, secure, and productive remote work environment.
SASE and Its Role in Digital Transformation
As organizations undergo digital transformation, SASE plays an increasingly crucial role. For businesses looking to harness the potential of the cloud, Internet of Things (IoT), and other digital innovations, SASE provides the secure, robust foundation on which these technologies can thrive. SASE supports ambitious digital strategies by addressing the complex security and networking demands that accompany such transformative initiatives. SASE enables organizations to capitalize on new opportunities with agility and confidence by interweaving security and networking into a single fabric.
The impact of SASE on digital innovation can be seen in its ability to facilitate seamless connectivity for an increasingly distributed set of applications and services. Organizations that embed SASE into their digital transformation efforts can anticipate a future where the harmony between security and accessibility is an accelerant rather than a bottleneck for growth and innovation.
Comparing SASE to Traditional Security Models
In the face of increasing cyber threats and the explosive growth of cloud-based assets, traditional security models show their limitations. Unlike these antiquated frameworks, SASE stands out by delivering an integrated solution that addresses the dynamic nature of contemporary cyber environments.
Businesses that move from conventional models to SASE enjoy a host of enhancements, notably in the realms of flexibility, control, and ease of management. The whole notion of cybersecurity is recalibrated within the SASE paradigm, unlocking new levels of operational agility that were once unthinkable.
The success stories of enterprises that have transitioned to SASE are a testament to its transformative potential. These cases illustrate the viability of SASE over traditional security models and the tangible benefits in resilience, performance, and manageability accompanying its adoption.
How to Implement SASE in Your Organization
Organizations must embark on a strategic planning process to successfully navigate the transition to SASE. It includes analyzing the current state of their network and security infrastructure, engaging with stakeholders to define clear objectives, and developing a phased approach for roll-out. Considering factors such as the size of the enterprise, existing technological foundations, and unique business needs, it is essential to tailor a SASE implementation that delivers optimal value. Establishing a clear timeline, with defined milestones and success metrics, can guide the organizational shift towards a SASE-enabled environment smoothly and effectively.
Another critical success factor is aligning executive leadership, IT departments, and end-users around the benefits and changes SASE will introduce. This holistic approach guarantees technical readiness and ensures that the broader organization is prepared for the cultural and operational shifts accompanying the implementation of SASE.
SASE Case Studies and Success Stories
Diving into the success stories that typify SASE adoption provides invaluable insights. These narratives reveal how enterprises across different industries have navigated the complexities of SASE deployment, surmounted the associated challenges, and harnessed their capabilities to drive substantial business improvements.
Front and center in these case studies are the distinct uplifts in security measures, network management efficiency, and operational resilience these organizations have achieved due to embracing the SASE model. These success stories clearly show SASE’s potential and offer a blueprint for businesses undergoing similar digital and security transformations.
Sum Up
In sum, SASE represents more than a technological innovation — it is a strategic enabler that empowers organizations to operate with greater freedom, efficiency, and assurance in the cyber domain. Ensuring that SASE remains at the forefront of the fight against cyber threats while supporting modern business operations requires its ability to adapt to the ever-changing digital landscape.
The astute adoption and continuous refinement of SASE systems will likely be a differentiating factor for organizations aspiring to maintain a competitive edge and an impeccable security record in an increasingly connected world.